Keep your Oracle Database safe, and secure
Oracle database offers a wide complement of built-in and optional components for addressing database security – to ensure data privacy, protect against insider threats, and enable regulatory compliance.
Eclipsys can help you enable these components with the following services:
Database Security Audit/Assessment
A review of your security requirements against your current environment and database deployments to provide you a report that identifies areas of concern, compliancy issues and suggested improvements for your infrastructure – as well as our best practice recommendations on how to address them.
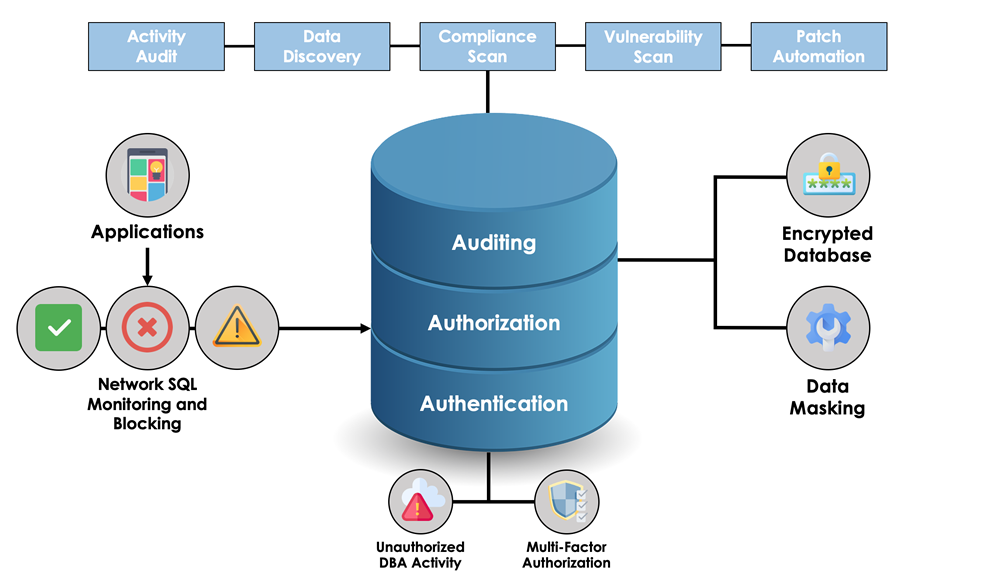
Oracle’s Maximum Database Security Architecture
Database and WebLogic Patching
Customers’ systems can be exposed to additional risk because they just haven’t applied the latest security patching to their systems. Eclipsys can assess how current your patch set is on your infrastructure and plan and execute database and WebLogic security patches for you.
Deployment of Oracle Database Security Products
Eclipsys can augment your standard database security by implementing the following Oracle database security products:
- Advanced Security/Data Encryption (TDE)
Protects your data at rest, by encrypting data on disk including your RMAN database - Audit Vault
Provides an enterprise security monitoring and auditing platform, and compliance to HIPAA and other standards - Database Firewall
Creates a defensive inner-perimeter that monitors and enforces normal application behaviour, helping prevent SQL injection, application bypass, and other malicious activity from reaching the database - Data Masking
Ensures confidentiality by preventing sensitive or confidential parts of the information from being disclosed to unauthorized parties - Database Vault
Implements preventive controls on privileged users, to prevent insider attacks
Our consultants can help you understand how each of these components works to eliminate internal or external threats to your database, in order to address your security challenges and help you implement a security solution that provides the right balance of enterprise protection with your available budget.

